Second, system function and system flow
1. System function introduction 1) Vehicle certification According to the escort plan, the escort business personnel arrives at the designated area of ​​the bank with the cashier in the business network. At this time, the smart escort engine at the outlet sends the escort truck to the voice prompt outlet management personnel, and the escort truck arrives. The intelligent escort host display on the screen displays the photos of the escort personnel and the occupants of the vehicle and the personnel information. The management personnel can directly identify the vehicle and the detaining personnel.
2) After the escort person's identity verification and face grab comparison are completed, the escort personnel will perform fingerprint authentication on the smart escort extension at the linkage door, and at the same time capture the facial photos of the certification personnel through the camera on the extension. Once the verification passes, The system automatically displays the authenticated escort personnel information and captured facial photos on the smart escort host display screen. The management personnel can easily compare the original storage photos of the escort personnel with face photographs captured in real time. The system carries out the dual authentication function of automatic fingerprint biometric identification and artificial photo comparison to realize joint control and joint control, and to achieve the combination of physical defense and technical prevention.
3) Business Commissioner Identity Authentication When the escort vehicle, escort personnel, and cash box certification are completed, the bank sales representative needs to perform fingerprint identification to confirm that the transaction is successful, the smart escort host displays a photo of the business commissioner to determine, and the voice broadcast: “Business The Commissioner xxx is certified to be successful. At the same time, the authentication information is automatically transmitted to the management center for storage, and the central server voice broadcast prompts to realize the responsibility to the people.

4) The schedule management center vault can schedule the debit schedule every day, select the corresponding “debit banknotes, debit notes, outlets, debit notes, and receipt information†and deliver the handover task to the network point intelligent escort host.
5) Handover process Packing personnel certification, vehicle certification, cash box certification, salesperson fingerprint confirmation information packaged into a message upload center, (with the entire handover process as a package), the monitoring center received similar e-mail information, such as the need to understand the entire handover details Information, double-click to open the package 6) Transfer of money box According to the escort plan, the escort business personnel first go to the vault (or business outlets) handover area to complete the personnel certification, and the vault (or outlet) management personnel open the isolation door and the debit keeper in the vault (or outlet ) The transfer area starts the transfer of the cash box. At this time, the system automatically identifies the number of the transfer box and the number of the cash box, generates a transfer report, prints the transfer report directly through the printing device, and deposits money with the vault (or outlet). Trace, confirm handover completed.
7) Illegal authentication alarm:
When someone authenticates the fingerprint five times in a row, the system automatically restarts the task and sends an authentication error alarm message to the management center.
8) Case wrong box alarm:
When the debenture holder raised the wrong money box, the money box belonging to the A network point was sent to the B network point, and the system automatically reported an alarm.
9) Lost alarm:
When the number of moneyboxes sent to the bank and the number of dispatched plans cannot be matched, the system will automatically call the police.
10) Banknote jumping alarm:
When the cash car is not handed over according to the established line, the system will automatically alarm.
11) Personnel Information Import Personnel information can be collected from the personnel collection system of the escort company and imported into the central software in an encrypted file format, thus avoiding the network restrictions of the bank and the escort company and collecting troubles.
12) Risk handling The handover process is normally normal and there is no need to alert the software. When there is something wrong with the handover process, risk management and software alerts should be started.
13) Importing of disconnected network tasks When problems occur in the banking network, the system can download tasks by encrypting the mobile terminal. After the network reaches the network, the system performs interception work after the import task is performed on the authentication front-end machine.
14) Fingerprint Management:
Fingerprints can be collected in various ways such as central collection and front-end dot collection.
15) Intelligent voice human-computer interaction:
Throughout the entire handover process, voice and graphic prompts and announcements are made. The outlets display operations based on voice prompts and graphic texts, making the use process simple and convenient.
16) Central software TTS voice prompts:
When there is a handover record or an alarm event, the central server automatically broadcasts voice reports to remind the on-duty personnel to handle the operation.
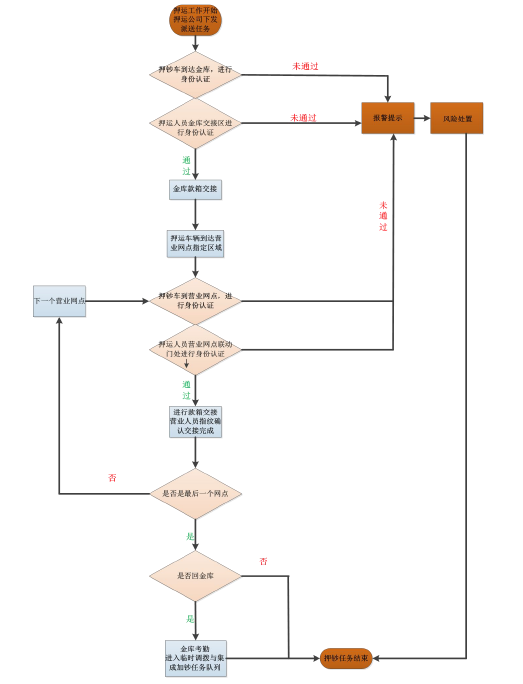
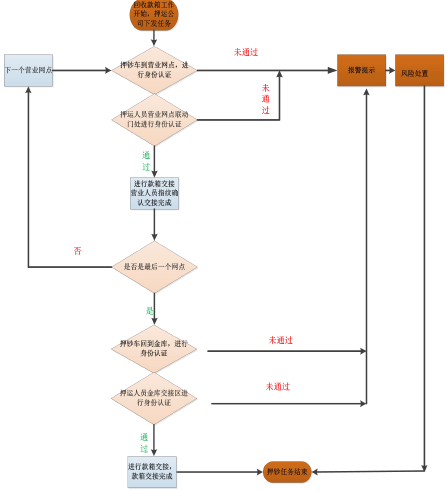
2. System Workflow 1) Delivery process The escort company dispatches tasks and issues the task. The escort truck arrives at the central vault, the escort personnel conduct identity verification, the central vault performs the transfer of the purse, the escort vehicle departs to the delivery network, and the network voice prompts. When the teller arrives, the detainer arrives at the linkage door to perform identity verification. After the success, the business outlet opens the linkage door. After the demobilization personnel arrive at the network handover area, the system performs the identification of the receipt box. After the completion of the handover, the business network staff will confirm the handover and transfer the connection. The work is completed. The punt car goes to the next outlet.
2) Recycling money box process The company's arranging task of repatriating money box and issuing the task shall be issued. The money teller will start to arrive at the designated outlets. The network will voice the reminder to the arrival of the telling machine. The demobilization personnel will arrive at the linkage door to perform the authentication. After the success, the business outlet will open. After the linkage door was opened and the demobilization personnel arrived at the network handover area, after the handover was completed, staff at the business outlets confirmed the handover and completed the handover. The remand car was returned to the central treasury, and the vault reminded that the pledger arrived and the detaining staff had to verify their identity. After the success, the detainees arrive at the handover area and the system automatically conducts the identification of the case. After the transfer is completed, the vault staff confirms the handover and the handover is completed.
3) Temporary transfer or central banknote increase tasks The task of temporary transfer or central banknote increase is the same as above.
3. Diagram of the electronic identity authentication system for escorts (vehicles and cases)
A sheet metal stamping operation is one in which sheet metal is cut and formed into a desired shape or profile. Although a sheet metal stamping process may utilize numerous types of special machines, three basic items are essential: the sheet metal from which the part is to be made; the stamping press; and the stamping die.
With the exception of a specialized sheet metal stamping process commonly referred to as hot stamping, most sheet metal stamping operations involve cold forming. This essentially means that no heat is intentionally introduced into the die or the sheet material. However, keep in mind that although stamping is a cold-forming process, heat is generated. Cutting or forming sheet metal creates friction between the die and the metal-much like the friction and heat that occur when you rub your hands together.
Benefits you can enjoy when you work with our team of experts include:
Consistency: Stamping produces a high volume of finished products made to precise specifications with matching consistency over large batches and multiple production runs.
Adaptability: With vertical integration for our processes, we can respond to issues and change your order in a fraction of the time it takes when using an outsourced provider.
Cost: Metal stamping is already a cost-effective way to produce goods. Our services make it even more competitive by eliminating unnecessary expenses and controlling material waste.
Speed: At Fairlawn Tool, Inc., we specialize in high volume metal fabrication. Our processes and metal stamping capabilities are all as efficient as possible to ensure short lead times and rapid product delivery

Sheet Metal Stamping,Custom Metal Stamping,Custom Sheet Metal Stamping,Precision Sheet Metal Stamping
Suzhou FCE precision electronics Co., LTD , http://www.fcesz.com