Big Data Security is a comprehensive discipline that involves many disciplines such as cryptography and data mining. The main view library is mainly deployed in the public security private network and the video private network, which is physically isolated from the Internet, but the security issue cannot be ignored.
Component login authentication
User authentication and authorization management is designed to authorize legitimate users to access the system and access the database while protecting these data from unauthorized access. The view library uses Huawei's big data platform FusionInsightC70 to integrate a complete security authentication framework to help users to authenticate and record all the tasks submitted by authenticated users. This prevents illegal users from logging in and can effectively monitor user operations. , improve the security of the system. For the access control of big data components, it is an important part of data security. For this problem, Huawei's FusionInsight platform adopts Kerberos authentication technology. Kerberos is a third-party protocol for security authentication. It adopts traditional The shared key method implements communication between the client and the server in an environment where the network environment is not necessarily secure, and is applicable to the Client/Server class model. The FusionInsight platform can also assign operating rights to different components according to different users. To a certain extent, it limits the components that each user can operate, especially the related authorization of storage data components, which directly affects the security and maintainability of data.
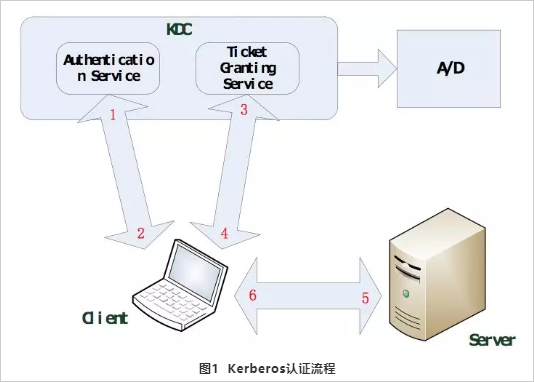
Figure 1 Kerberos authentication process
As shown in Figure 1, the Kerberos authentication process is divided into the following three steps:
(1) The client (Client) interacts with an Authentication Service (AS).
(2) The Client interacts with the Ticket Granting Service (TGS).
(3) The client interacts with the server (Server).
Compared with Kerberos, HTTPS may be more familiar. It is through the certificate and asymmetric encryption, so that the client can securely access the server, but this is only the client security. Through verification, the client can guarantee that the server is secure. Reliable, but the server can not know whether the client is safe and reliable, which is also a feature of the Internet. Kerberos supports two-way authentication, which ensures that the server accessed by the client is secure and reliable, and the client that the server responds to is secure and reliable. But to prove that both Client and Server are reliable, it is necessary to introduce a third-party notary platform, namely AS and TGS.
The client requests the Kerberos service to obtain the permission to access the server. When the Kerberos gets the request, it first determines whether the client is trustworthy, and then distinguishes the blacklist and the whitelist in the client whitelist (Account Database: AD). Client, after successful, the AS returns the TGT to the client.
When the client obtains the authentication ticket (ticket grant ticket: TGT), it continues to request Kerberos to gain access to the server. When Kerberos gets the request, it judges that the client has this privilege and gives the client ACCES through the TGT in the client message. After the client obtains the ticket, the server can finally access successfully. This ticket is only for this server, other servers require a TGS application. A few key points to explain throughout the certification process are:
(1) The whole process TGT acquisition only needs one time. There is a concept of timeout. The TGT is valid within the time range. That is to say, in general, the server only needs to get the ticket directly.
(2) The whole process uses symmetric encryption, which has a performance advantage over asymmetric encryption.
(3) Kerberos user management is very convenient, only need to update the list in AD.
The communication of the whole process is encrypted. Here we design two layers of encryption, because all authentication is through the client, which means that Kerberos does not directly interact with the server. The reason is that Kerberos does not know the status of the server, and cannot guarantee. At the same time, the order of communication with the server and the client is forwarded by the client, which allows the client to guarantee the sequence of the process.
The first layer of encryption, Kerberos encrypts the data sent to the server, preventing the client from getting tampering with the information. The second layer of encryption, Kerberos encrypts the data sent to the Client to prevent other network monitors from obtaining this information. The same is true for the communication between Client and Server.
Data traceability technology
With the continuous development of information technology such as Internet of Things, big data, cloud computing, etc., data sources and data dissemination methods are more extensive. Only a complete record of the source and dissemination of data can facilitate the later data mining and data identification. Data Provenance technology has been extensively studied in the database field long before the big data concept emerged. The basic method of data traceability is the marking method. In the video image database, each video image data marks the source system of the data. When the system data is detected abnormally, the origin of the data can be located through data traceability. In the docking library standard, the interface can receive information about the docking system in the data header field according to the interface, and the data is tagged and stored in the database. This method can effectively mark each source data, which is convenient for later. Data traceability processing, and the related application of data from related sources and the mining of other useful information.
Software encryption technology
The software encryption lock is an encryption operation based on the AES algorithm, which can perform digital authentication before the startup of the view library software, and authenticate the identity by the software encryption lock, thereby preventing illegal login by illegal elements. The AES algorithm is based on permutation and permutation operations. The permutation operation is to rearrange the data, and the permutation operation replaces one data unit with another. AES uses several different methods to perform permutation and permutation operations. The AES algorithm is an iterative and symmetric key grouping cipher that uses 128, 192, and 256-bit keys and uses 128 bits (16 bytes) for packet encryption and decryption of data. Unlike public key cryptography, which uses a key pair, symmetric key cryptography uses the same key to encrypt and decrypt data. The number of bits of encrypted data returned by the block cipher is the same as the input data. Iterative encryption uses a loop structure to repeatedly replace and replace the input data in the loop.
Control Valve,Idle Air Control,Idle Control Valve,Idle Air Control Valve
Yantai Tianbing Construction Machinery Co., Ltd , https://www.tbbreaker.com